 A few years ago, applying for personal loans was a difficult job. The process was Know Your Customers (KYC) difficult and a complicated process that required a massive number of documents. If you’re looking to take out a cash loans for emergencies, there is no need to consider the phone you used to call. Many […]]]>
A few years ago, applying for personal loans was a difficult job. The process was Know Your Customers (KYC) difficult and a complicated process that required a massive number of documents. If you’re looking to take out a cash loans for emergencies, there is no need to consider the phone you used to call. Many […]]]>
A few years ago, applying for personal loans was a difficult job. The process was Know Your Customers (KYC) difficult and a complicated process that required a massive number of documents. If you’re looking to take out a cash loans for emergencies, there is no need to consider the phone you used to call.
Many lenders, banks, financial institutions, and online lenders have realized the importance of technology in making life easier for their customers. They have created individual loan mobile applications accessible on the internet and are available for download on mobile devices.
Installing a mobile application on your smartphone to have instant financial protection is a wise choice. If you’re about whether or not to install the personal loan application, Here are seven reasons to download it now.
- You could apply for a personal loan in the event of emergency cash.
A personal loan application is equivalent to having a bank account in your pocket. If you require, you know you’ll have to go. All you have to do is go to your pocket, pull out your mobile phone, and make an application to get a loan personal via the mobile application.
The personal loan application acts as a backup that you require financial assistance.
- It will save you time and energy.
Instant loan applications give you all-hours access to the services. When you’re on the move in your home, at work, or even working, it is possible to apply for personal loans at the touch of the button. You needed to go to the bank’s branch to get a loan in the past.
Personal loan applications have made loan applications paper-free entirely thanks to this eKYC function that helps you save time and energy.
- The app is secure and secure.
Regarding mobile loan applications, you are concerned that your security and privacy are entirely acceptable. It is essential to know that mobile loan applications are completely secure and reliable. There is no chance of losing your funds, but you should protect your personal information with a safe password.
MoneyTap employs the latest encryption techniques to ensure your personal and financial data is secure.
- Fast approval and instant cash access within your application
Online applications for personal loans are much quicker. Online loan applications are simple and easy to use. After you have applied via an app loan decision is taken within just a few minutes, and you get a cash-based loan within your app quicker than you could ever imagine.
- Keep track of all transactions.
It’s simple to track the online borrowing you make. Mobile loan apps offer an excellent user experience. You can review your account details to find out the amount of debt you have and how much you’ve borrowed, and your due dates.
You can receive automated reminders of your payments, as well as email or SMS reminders so that you do not forget to make a payment.
- Access to all-time money and other information
You can access 24/7 cash at the touch of a button. You can perform direct transfers to your bank account anytime during the day. The loan amount you take out is available for any personal expenses you might have, at any time you’d like, and at whatever date you wish to use it.
Personal loan apps are an enormous help, particularly when traveling on business or private trips. With cash readily accessible on your smartphone that you can access any time, from any location, and at any time, you don’t need to fret about bringing cash along on your trip.
- A personal line of credit may be used to cover various individual costs.
Whatever your expenses are, whatever they are, you can take advantage of a personal credit line that anyone with a mobile phone can access. You can buy an iPhone through EMI or an e-marital loan, get your start-up up and running by securing a business loan or travel the world with a travel credit. A personal loan application within your pocket will go an extended way to making shopping straightforward.
Now that you understand the reasons to have an app for personal loans for your smartphone install MoneyTap, an innovative mobile application that lets you complete all of your loans quickly by pressing the button.
]]> [ad_1] AWS this week declared that Amplify Studio, a fast app builder previewed at the re:Invent conference at the end of the year, was ready for production. There have been a number of improvements since the preview, including the addition of new target platforms, whereas the initial preview was only for React web apps. Amplify […]]]>
[ad_1] AWS this week declared that Amplify Studio, a fast app builder previewed at the re:Invent conference at the end of the year, was ready for production. There have been a number of improvements since the preview, including the addition of new target platforms, whereas the initial preview was only for React web apps. Amplify […]]]>
[ad_1]
AWS this week declared that Amplify Studio, a fast app builder previewed at the re:Invent conference at the end of the year, was ready for production. There have been a number of improvements since the preview, including the addition of new target platforms, whereas the initial preview was only for React web apps.
Amplify Studio now builds apps where the front-end is JavaScript or TypeScript using React, View, Angular or React Native, or Google’s cross-platform Flutter, or Android using Java or Kotlin, or native iOS using Swift.
A notable absentee is Microsoft’s .NET platform. The generally available version also adds new features, including event handlers for UI events and component theming. Amplify Studio is a visual builder for the AWS Amplify framework, although not everything is included with Amplify.
The idea of Amplify Studio is to provide a visual environment to quickly create complete applications. It is most comfortable when used with the cloud-based Figma design tool and the React framework. Developers or designers can keep visual components in Figma and sync them to an Amplify Studio project. Visual components can be data bound.
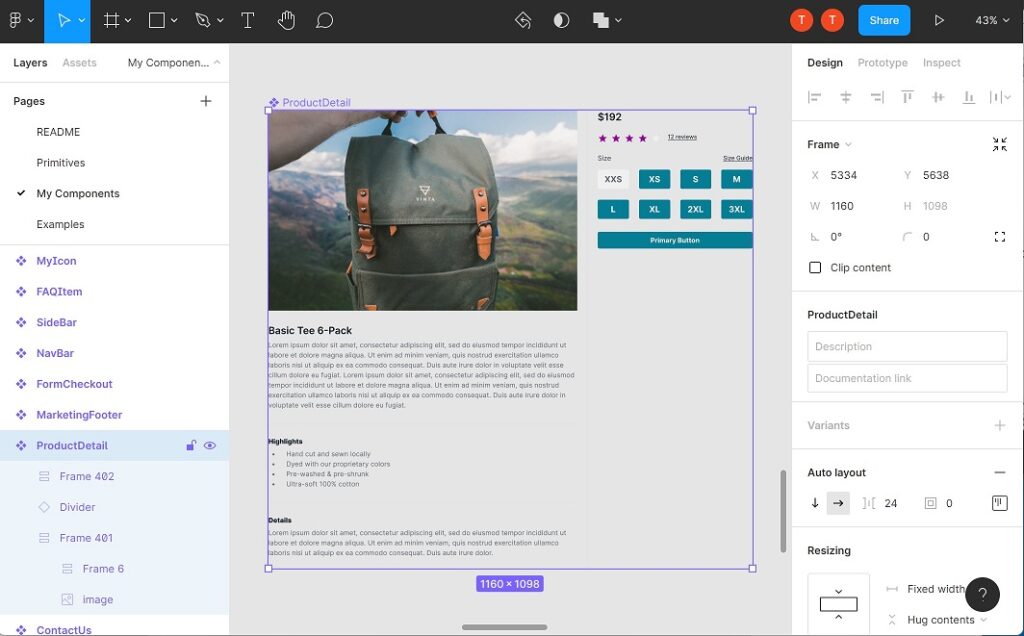
Amplify Studio includes tools that summarize database management. Developers build a data model including entities, fields, and relationships. Amplify Studio provides DynamoDB tables on its cloud platform and a local DataStore that automatically syncs data between a mobile or web app and DynamoDB. File storage is also integrated, using the AWS S3 service.
Authentication and authorization is also provided, using the AWS Cognito service, which can also be with Apple, Facebook, Amazon, or Google IDs. Authorization features include the ability to create user groups and add rules that define their level of access.
Although there is no charge to use Amplify Studio itself, it is deeply integrated into the AWS platform and users pay for the resources consumed. One of the goals of the tool is undoubtedly to attract more users for various services, and the built-in tools make it easy to add features based on Amazon API Gateway (Graph and REST API), Lambda functions, analytics with Pinpoint (marketing communications) and Kinesis (data delivery), AI and ML services for things like text-to-speech, image recognition and chatbots.
While Amplify Studio looks promising for rapid development on the AWS platform, developers have complained about quality issues with the underlying Amplify framework. “Common use cases were not well managed, deployment failures were common, overall architecture was actually less consistent when using amplification than just constituent AWS services directly”, mentioned one developer on Hacker News, while another Noted that “deployment errors are fortunately rare these days, but things that should be easy are hard, and there are many seemingly obvious use cases that the Amplify CLI doesn’t handle”.
Developers can consult the GitHub repository assess the manager’s progress towards maturity.
[ad_2]
Source link
 [ad_1] Calloquia is poised to redefine the legal sector with technologies that improve the delivery of legal services while improving access to justice. Our company was founded by a litigator from a leading law firm to solve the day-to-day problems of the legal profession. Our mission is to harness the power of technology to make […]]]>
[ad_1] Calloquia is poised to redefine the legal sector with technologies that improve the delivery of legal services while improving access to justice. Our company was founded by a litigator from a leading law firm to solve the day-to-day problems of the legal profession. Our mission is to harness the power of technology to make […]]]>
[ad_1]
Calloquia is poised to redefine the legal sector with technologies that improve the delivery of legal services while improving access to justice. Our company was founded by a litigator from a leading law firm to solve the day-to-day problems of the legal profession. Our mission is to harness the power of technology to make the justice system more fair, accessible and efficient.
We are looking for seasoned developers to join our team. It will be a dynamic and rapid role with a multitude of responsibilities. You will help us shape the future of Calloquy and be a key member of the team to help us launch the business.
Calloquy is recruiting a team of developers in this process and we encourage applicants with diverse skills to apply. This may include in-depth specialties in the areas listed below as well as varying levels of experience.
Main Responsibilities:
- Play a lead role in the development team in support of the overall platform lifecycle.
- Actively work with senior management to develop and refine the application to support the functional requirements.
- Actively collaborate with the DevOps team on related components including infrastructure, automation, deployment, and security.
- Support efforts to establish and ensure compliance with the security and safety measures necessary to protect confidential and highly sensitive information.
- Support efforts to develop and implement quality assurance processes to ensure feature sets are ready for customer use.
- Help develop and promote the company’s culture of success and dedication to customer service.
- Other assigned tasks.
Knowledge, skills and abilities:
- Solid experience in developing web applications using PHP.
- Solid experience with the PHP Laravel framework.
- Strong experience with JavaScript, in particular the React framework.
- Experience in HTML and CSS.
- Experience in database management, in particular MySQL.
- Specific knowledge or experience with AWS CodePipeline and AWS CodeBuild.
- Familiarity or experience with standard web security components (OWASP Top 10) such as access control, XSS and SQL Injection.
- Able to support and design systems that respect security and process compliance.
- AWS certifications are beneficial.
- “Can do” attitude and “do it” mentality.
- Ability to work independently and exercise good judgment.
- GIT or similar version control like Jenkins etc.
- Cloud mindset: understanding of containers, CI / CD and Kubernetes clusters.
- Passion for working with cross-functional teams including product, design, analysis, marketing and sales teams.
- A humble team player who actively participates in the development of his peers.
Education and experience:
We suggest that to be suitable for this role you have demonstrable skills in most of the technologies listed above, and approximately 5 years or more of relevant experience.
We value candidates who can implement our vision and help us create a platform that changes the industry for the legal industry. What is important to our mission is that you can work in the technologies listed here, rather than in specific training. If you have a computer science degree, great. Attended a bootcamp? Marvellous. Have you been a consultant for years and have the portfolio to demonstrate? You are welcome to apply.
Our values and beliefs:
Work for the collective good
We are a for-profit company with a social mission. We strive to promote the collective good of our employees, our customers, our shareholders and justice.
Think big
We strive to create a fair legal system that protects the rights of all individuals and promotes the rule of law in a cost-effective manner. Bring in your big ideas and get ready to implement them.
Do the right thing
Doing the “right thing” is never the wrong thing. Always strive to do what’s right for our customers, for our business, and for the rule of law.
Dignity for all
Diversity, inclusion and belonging are the key to our success. We aim to create more equal access to the justice system, and we foster a culture that is inclusive and supports all team members in achieving their professional goals. We value our customers and treat our colleagues with respect.
Solve the problem
When you see a problem, don’t assume that someone else is already working on the solution. We all take responsibility for identifying and resolving issues for our stakeholders.
Learn from our mistakes
We are all human and we will all make mistakes. Join them. Learn from them and grow.
Gain someone’s trust
Trust is essential to the success of our business. In every action we take, we must determine whether it is the action that will deepen or destroy trust.
Take action
We have ambitious goals and we are actively working to achieve them. The willingness to act, even in the face of uncertainty, will be essential to our success.
Hire and retain the best
Our people are our most valuable asset. We need to have the processes and systems in place to ensure that we hire and retain the best. Period.
Help others succeed
We must all strive for constant professional development. Professional growth requires great mentors, thoughtful leaders, and a desire to see others succeed.
How to register:
Email us your resume and a note of interest to tell us about yourself and why this position may be suitable at [email protected]
Calloquy embraces diversity and is an equal opportunity employer. We are committed to building a team that represents a variety of backgrounds, skills and abilities. We believe that the more inclusive our team, the better our work will be.
[ad_2]
Source link